Product Cybersecurity
Secure product development
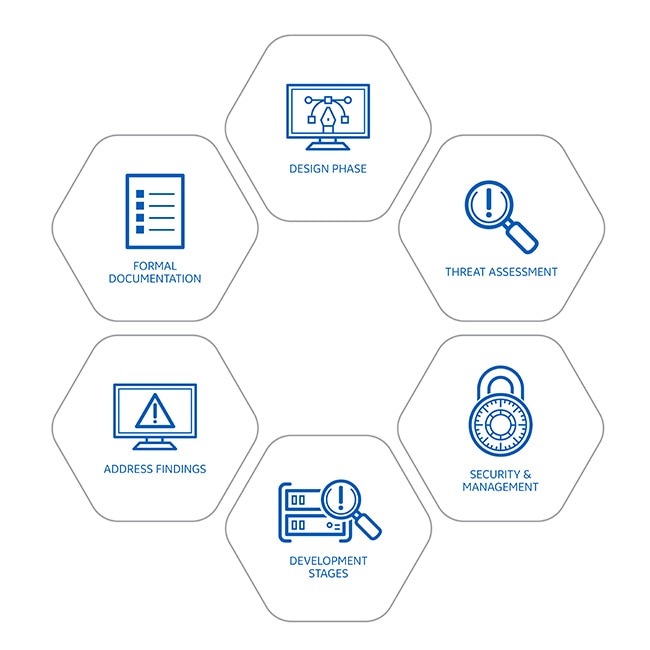
Address findings
Assessment findings are reviewed by the cybersecurity team, and are either fully addressed prior to release, or in rare cases with lower associated risks any residual risk is formally risk-accepted and documented.Design phase
During early development, we determine what the product or solution architecture will be based on its intended function, how it will be used, and what environment it will operate in.Formal documentation
Prior to release to the market, documents are created to describe any deployment-related controls for the customer to implement. A standardized hand-off of residual risk is a formal part of this documentation.Full threat assessment
Performed based on initial design and operating environment using industry standard threat models that specifically tailored to the clinical environment in which a device operates.Quality management system checkpoints
Throughout the development process, control implementation is continuously monitored and controlled.Final development stages
Manual review, vulnerability scans, static and dynamic code analysis, and several phases of internal and external penetration testing are all performed to ensure full implementation and help secure our products throughout their lifecycle.




